Since the 2000s, the information age has reinvented almost every aspect of our lives. Your phone is no longer just a calling device. The smartphone is your entry into a world of options, interactions, and possibilities. The same goes for your watch, car, television, and even your fridge. The internet of things (IoT) is expanding our digital sphere and making it easy to access information – sometimes without even touching a button. And the number of IoT-connected devices is only going up. But with great power comes great responsibility, and even greater risks.
We share a lot of information online without even understanding the consequences. E.g., while installing an app, we share our details and agree to terms and conditions without even reading those. These companies who take the information sell your details to a third-party that is a multi-billion dollar industry. Our identity, location, behavior and other details are used for target advertising, phishing emails, etc.
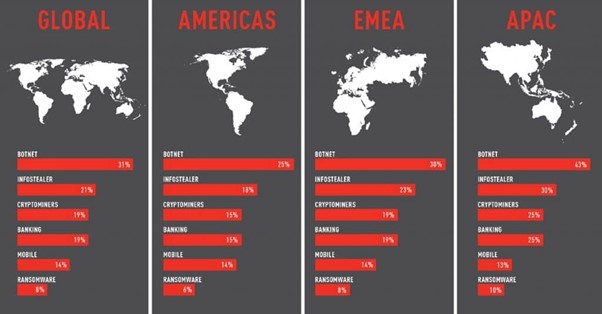
Cyberattack trends by region in 2021. Source: Check Point
Hackers and fraudsters are eyeing the weak link to gain control of your digital assets. There seems to be a new data breach in the news every day. And with the introduction of 5G, the threats are set to increase multi-fold. This is becoming a major concern for businesses and individuals alike. Yet, despite awareness, a small mistake can cost us dearly.
Is there a silver bullet? The answer is NO.
While companies are data-driven, we, the users, can work on securing our interactions in the digital world. In a world that is increasingly digitized it is more important than ever to ensure that our digital world is safe. By building a safer digital world we can protect ourselves and our loved ones from online threats. There are a number of ways to building a safer digital world, and each of us can play a role.
First, be aware of the risks. According to Experian’s Global Identity and Fraud Report, 1 in 4 APAC consumer was a victim of online fraud. With the majority falling prey to fraud on social media sites and applications. Phishing and all its forms (whaling, angler phishing, spear phishing, smishing, and vishing) is still the most common attack vector of cyberattacks. According to Norton, the top most cyber threats to avoid in 2022 and in the near future include cryptojacking, mobile-focused cybercrimes, IOT-focused cybercrimes, social engineering attempts, and stalkerware on your devices.
Second, practice basic cybersecurity hygiene while navigating the digital sphere.
- Avoid using public Wi-Fi
- Do not share any confidential information with unknown people or unauthorized sites
- Change your passwords frequently and don’t reuse passwords across applications
- Do not install unwanted apps
- Patch device periodically
- Keep updating the app version
- Use two or multi-factor authentication
Third, research and invest in security solutions that can help you create and implement robust security measures.
- Use a Virtual Private Network (VPN) – Working from home can make people relax a bit when it comes to security and privacy. Fortunately, VPNs are here for online security and privacy. It adds a layer of security by encrypting your connection to the internet and protecting your data/browsing history safe from prying eyes (E.g. an internet service provider, third-party advertisers, and malicious players). VPNs also help getting past network restrictions and firewalls while maintaining your privacy online. There are several free and paid VPN providers in the market, and choosing the right one can be tricky. NordVPN, a premium VPN provider, provides a checklist of what to look for in a VPN – mainly operating system support, number of servers, transparency, speed, and additional security features such as threat protection, multi-factor authentication, etc.
- Use Endpoint Detection and Response (EDR) – EDR is an investment for large to medium-sized businesses. While VPN protects your connection to the internet, EDR monitors, records, and protects your endpoint devices. Many may compare EDR to antivirus, but it’s much more than that. For businesses EDR is key to better endpoint visibility, network monitoring, insights, and intelligence, including behavioral analytics. A good EDR tool would improve cybersecurity resilience with automatic detection and containment of any cyber incident.
The security of your digital world and data is an evolving process. New breaches and attack vectors would continue to emerge as technology evolves. But if you practice basic cybersecurity hygiene and invest in the right tools, you will greatly reduce your attack surface.
