
If we had to describe the current weather of the digital sphere, an apt forecast would be ‘mostly cloudy’. It was partly cloudy back in 2015, with 30% of the world’s corporate data stored in the cloud and 1.1 billion people using personal clouds such as Dropbox, Google Drive and iCloud. Fast forward to the present day, and in a mere 8-9 years, those figures have ballooned to 60% of the world’s corporate data, and 2.3 billion people on personal clouds. In fact, 92% of enterprises presently host at least some of their IT environment there.

Why so? Because scale, flexibility, economics and ease of adoption make cloud a highly desirable option for managing organizational and personal data. There’s no doubt that its scope is unprecedented – most of the streaming platforms we frequent and the games we play have been developed solely on the cloud. However, the danger lies in the fact that every asset in the cloud can be exposed to the Internet, simply because, well, you are accessing it over the Internet.
This danger is magnified in organizations because many of them think cloud security is comparable to on-premises security. But that’s far from the case – the cloud is a different beast, and before getting onto it, one has to stringently manage and strategize what goes onto it and what doesn’t, what’s critical and what’s not.
It’s an oversight that is becoming increasingly widespread and costly. 80% of companies have experienced at least one cloud breach in the last year. And on the off chance you are breached, the average cost of a data breach in organizations using private cloud is $4.24 million, which balloons to $5.02 million for those using public cloud like AWS, GCP and Azure.
There are quite a few risks associated with the cloud, and your strategy should be designed to mitigate them. Misconfigurations are a key risk, with Gartner saying they cause 80% of all cloud data breaches.
The biggest fallout of this came in the summer of 2019, with the now infamous AWS Capital One breach. A former Amazon employee named Paige Thompson created a scanning software tool that identifies cloud computing servers with misconfigured firewalls. Due to the misconfiguration, these firewalls accepted commands from outside. With this at her disposal, she launched a server-side request forgery (SSRF) attack that led to the PIIs of 100 million Americans and 6 million Canadians to be leaked. The estimated financial loss due to the hack was close to $200 million, and here’s the kick: AWS only discovered the incident from their Responsible Disclosure Program, not their regular cybersecurity operations. That, too, 4 months later.
Since we’re on the topic of AWS, another risk involves the shared responsibilities between CSPs and customers. Not being watertight in your distinctions for this particular risk leads to misalignment of duties, and that creates a blind spot for hackers to exploit. Here is the shared responsibility model AWS goes with these days:
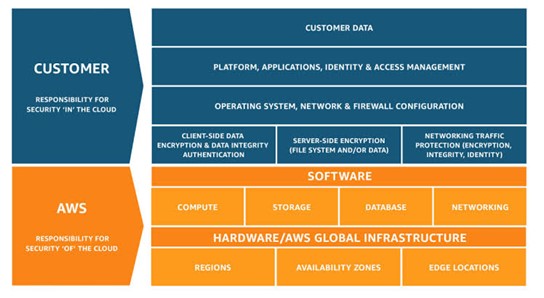
Improper identity & access management also becomes a big risk, as 83% of organizations have experienced at least one cloud data breach related to access. This makes it all the more important to have the right roles for the right users. And, of course, there are workflow risks, like vulnerabilities related to containers.
So, considering all these potential challenges, how would one go about creating a holistic cloud security plan? We believe the best plans should have these 10 elements:
Cloud Security Architecture & Strategy
Before moving onto the cloud, a comprehensive assessment of risk management and criticality has to be undertaken, which forms the backbone of a sound architecture & strategy. As shifting to cloud takes a long time to get right, we provide a security roadmap for you to successfully meet your goals.
Cloud Identity & Access Management
This is all about giving access and granting permissions to the right people, in the right amounts. IAM is an integral part of cloud security, as stolen credentials are often the easiest way for an attacker to gain access. A principle of least privilege should be adopted while figuring this out. Here’s another key tip: please, please, please keep your production and testing accounts separate.
Cloud Resource Inventory
This is a metadata inventory service that allows you to view, monitor & analyse all your cloud assets (hardware & software) across verticals, and gives you a snapshot of your entire inventory at any point in time. We have a host of matured as well as open-source tools to undertake this.
Provisioning Security
Cloud provisioning involves managing and configuring your IT resources (processing power, storage and network) to meet your organization’s needs. Adding a layer of security tools like firewalls, threat detection and encryption on top of this can help safeguard your assets.
Application Security
From securing SaaS, DaaS, code reviews and testing to safely deploying the app on cloud, application security is a continuous process that should ideally be automated across all steps. In fact, because of the complexities involved, the world is moving toward developer first security, which focuses on identifying vulnerabilities at the time of writing code itself, not at the time of testing or release.
Container Security
Containers are preferred to VMs because they are highly portable, use fewer resources and run consistently every time regardless of the environment. However, they have the capacity to create vulnerabilities, so the need of the hour is a robust security strategy integrated into the entire software development lifecycle. (SLDC)
Cloud Network Security Diagrams
This is extremely important for your cloud security, as it gives great visibility into how network and account resources are managed. Our solutions use Hava, which maps and subsequently creates informative data flow and network security diagrams that provide great insights into the structure of your cloud.
Logging & Monitoring
It is essential for all logs to be captured, and all incidents to be reported. This will give you all the necessary data to investigate & take subsequent action on the same.
Data Security
This peg goes about safeguarding the three types of data on your cloud – data in rest, data in motion and data in memory. Another factor to consider is how your regular encryption methods evolve when you’re dealing with cloud data.
Incident Management & Recovery
The last 9 elements were all about prevention, but what if the worst has already happened? This element is key in that scenario, as it creates plans for business continuity and data recovery in the case of an unfortunate breach.
Such a holistic security framework gives us the know-how to deal with the most prevalent issues when it comes to testing on cloud:

It also gives us the right tools for most of the issues currently plaguing the cloud sphere:

It all coalesces into a fully stacked security solution, where assets & resources across platforms are constantly sharing intelligence with one another. So, if you want to seamlessly lift up your organization into the cloud, without any of the growing pains and potential risks that come with it, contact us today to get started!
