
There have been 4 great Industrial Revolutions in the modern world.
The first one, back in 1784, focused on steam, water, and mechanization.
The second one in 1870 had electricity and mass production as its tenets.
The third one in 1969 took us to the digital age with electronics, IT, and automation at its heart.
And the fourth one is unfolding as we speak, with AI, machine learning, robotics and IoT being its key drivers. An exciting new period of digital advancement and knowledge driven by data.
Data that is now reaching unimaginable levels.
- IDC says the total global data stored will reach over 175 zettabytes by 2025. (A zettabyte is a trillion gigabytes, if you were unclear about how astronomical a figure that is.)
- 347.3 billion emails are sent out daily.
- In 2019, the number of IoT devices was 7.74 billion. That figure will triple to over 25 billion in 2030.
- In 2020, machine-generated data accounted for over 40% of the internet’s total data.
We’re in an age of exponentially increasing data being transferred at exponentially increasing speeds. And these exponential increases have led to an evolution in the very essence of data itself.
That has major implications for organizations that view data as its most important asset. Securing it is of tantamount importance, and for a long time, this was done by securing networks, servers, applications, and devices.
But we now live in a world where this approach is outdated. A world with more collaborations. More regulations. More data sharing. And more dynamic business environments, where remote work and cloud computing have become the norm. All this means more data now bypassing the traditional perimeters we set up to safeguard it.
We need a solution that can keep up with our data and the many, many places it inevitably ends up in. That brings us to
Data-Centric Security.
A set of technologies, processes, and policies whose focus is on protecting data throughout its lifecycle. A comprehensive strategy that focuses its strongest security efforts on your most sensitive information.
Its main elements include a central component called the management console, individual agents installed on specific assets that monitor file activity and send data back to the console, and finally, the supporting infrastructure to make it all work.
So, how do these myriad parts come together as a whole to protect your data?
It all starts with the data classification. Organizations deal with all types of data – structured (like your Excel sheets), unstructured (like the Word doc used to make this blog), public (like your brand offerings) and confidential (like the personal data of your consumers). Once you set the parameters of what comes under ‘sensitive data’, corresponding labels are applied to each file’s metadata. That enhances the performance of your security system in determining how a piece of data should be treated, handled, stored, and finally disposed of.
Once classified, we must be prepared for the probability of data leaving our infrastructure barriers. The best way of safeguarding data when it is no longer in our direct control is through encryption. This helps protect data against unauthorized access, whether it’s an authorized user accessing the data from an unsecured location, or actual attackers trying to breach a particular file. Core elements of the system like Data Loss Prevention (DLP) and Managed File Transfer (MFT) programs help secure files both in motion and at rest.
And speaking of authorized users, we come lastly to access control, which determines who has clearance for your protected digital assets, limits what people can do with files, establishes how long collaborators can access files and restricts sharing of content with unintended parties. Security is applied at an individual file level, subsequently following it to perpetuity. And access to protected data can be granted or revoked at any time, with all activities logged for auditing purposes.
The best way to approach access control is through the least privilege model shown below:
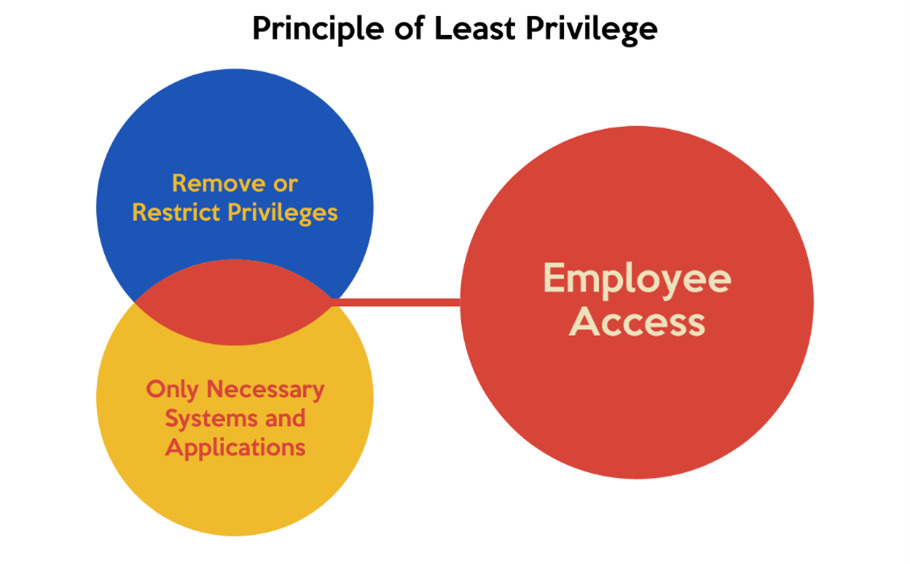
This principle gives users only those privileges essentially vital to perform their intended functions. A tech engineer will not have access to documents an HR manager has access to, and vice versa. An approach like this mitigates insider threats and, more pertinently, human error, which IBM claims is the main cause of 95% of cyber security breaches.
There are always challenges when deciding whether to take the leap on adopting a program like this. The ground realities and bottom lines businesses must deal with makes people think that such an all-encompassing solution will be near unfeasible to implement. But we believe our data-centric security packages have the power to transcend any worries you may have.
Your Doubts | Our Declarations |
I will have to start from scratch and upend all my current programs to incorporate this. | Not at all. Our solution can be seamlessly layered on top of existing systems. |
It will take a lot of time to implement this. | We undertake a phased approach, where we address your most critical security tricks first up before expanding onto additional user groups and processes. |
This will cost a lot of money. | No doubt, it is an investment. But when you consider the alternative of purchasing individual point solutions that inevitably create data silos and security gaps, our approach is a lot more secure and cost-effective. |
There’s no guarantee I won’t be breached, even if I adopt this. | There is. With our solution, it becomes impossible for sensitive data to exist in violation of your organization’s security policies. Your files are automatically scanned upon creation or modification and given appropriate protection. And if these files are shared in unsecure locations, or God forbid, stolen, the data in these files will remain safe from exploitation. |
So, are you ready to get started on securing all your data? Click here to get in touch!