There are two sides to the India growth story. A story deeply interlinked with the growing role of technology in our lives.
One side calls for appreciation.
- 18 countries now accept trade payments in INR, and 13 countries have signed an MoU to adopt UPI for their digital payments.
- $5 billion worth of iPhones were exported from India in the past year, and $10 billion worth of other smartphones – figures expected to exponentially rise.
- We just overtook the UK to become the world’s fifth largest economy, and we’re not done. The WEF projects us to be the third largest economy by 2037.
The other side calls for apprehension.
- Over 1.3 million cyber-attacks were reported across India in 2022.
- India is the second-most targeted country for cyber-attacks in the APAC region after Australia.
- India ranks third in the world for countries affected by password-stealing phishing campaigns.
The truth is our growing prominence in the world has resulted in a large target on our collective backs. A target that cybercriminals are trying to exploit with increasing regularity if recent breaches of AIIMS and Sun Pharma are anything to go by.
We’re dealing with an omnipresent, ever-evolving threat.
- Cyber-terrorism is on the rise.
- Hackers now use malicious AI to craft malware.
- More attacks are expected on critical infrastructure like power, transportation, and finance.
- Ransomware payments are now so commonplace that there are whitepapers on regulating them. Fact of the matter is, 92% of organizations don’t get all their data back from ransomware attacks. (Sophos)
- And cyber-insurance (whose premiums increased by 62% on average in 2022) and third-party cyber health checks are becoming near-necessities for organizations in the face of this threat.
This is a threat that, frankly, we simply aren’t prepared for.
- India faces an acute shortage of cybersecurity talent. 60% of Indian firms have unfulfilled cybersecurity positions, 42% say their cybersecurity teams are understaffed and 65% report difficulties in talent retention.
- Only 3 out of 10 companies have a formal security strategy, and 1 out of 4 have dedicated IT security teams.
- It doesn’t help that the most recent set of cyber laws in India are from the IT Act of 2000, long before IoT, cryptocurrency and, yes, AI hit their current heights.
So, how can you prepare for this? A good place to start would be adhering to the CIA triad shown below:

These are 3 sacrosanct covenants when it comes to dealing with your organizational data. Confidentiality keeps your data secure and private, integrity enables your data to be authentic, accurate and free from tampering, while availability ensures that your systems function as and when they should.
Okay, so you’ve got your building blocks. Now, you need a framework. Which brings us to something called ESG.
Enterprise Security Governance (ESG)
The benchmark for your organization’s data security strategy. It protects your assets, mitigates present & future risks, ensures compliance to the many regulations out there, and preserves the reputation of your organization in this ever-changing environment.
It helps you stay proactive, while the rest are being reactive. 4 core components of ESG help you stay ahead of the curve:
- Risk management performs a complete analysis of your business. Not only will it identify potential threats in your areas of interest, but it will also set a blueprint of what threats you may face in the future.
- Governance creates comprehensive SOPs for every specific task or incident, to ensure everyone in your company is on the same page in all situations.
- Compliance gets you on-side with all the regulations your company may face, whether it’s something overarching like GDPR, situational like state laws, or specific like your individual contractor requirements.
- And finally, security operations revisit and constantly monitor these procedures to keep you on top of the evolving digital landscape.
To make your company’s ESG all it can be, your people, processes and technology must work in unison. To that end, let’s stop for a second to do a quick exercise.
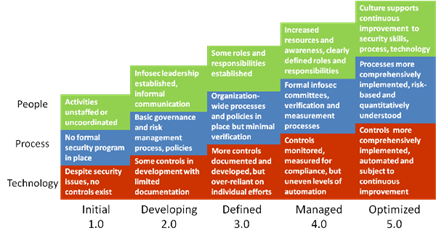
So, where does your organization currently fall in this scale? If you feel there’s room to optimize, ESG is the answer. There are many, many benefits to adopting one:
- It creates a better overall security posture for your company, as you’re constantly ready for threats.
- You have access to state-of-the-art technologies.
- That creates increased confidence from your customers & stakeholders.
- And gives you a sure shot competitive edge, especially if you implement it across the board for your third parties, too.
Sounds too good to be true, right? Something every organization should ideally have? Yet, there are many challenges to making ESG a widespread reality:
- It all starts with lack of stakeholder commitment, oftentimes stemming from a lack of awareness and cyber savvy from the top of the pyramid.
- It is a process that requires constant re-evaluation, which isn’t appealing for companies looking for a quick fix.
- Because of that, it requires a lot of investment, initially and periodically, which goes against the ‘one-time commitment’ culture.
- And it doesn’t help that India has a tricky regulatory environment, where state level regulations face off against government level regulations for companies operating in multiple locations.
But these shouldn’t impede you if your ultimate goal is to protect your organization and its assets.
And if that really is your goal, you’ve come to the right place. iValue has a comprehensive, 3-pronged ESG approach consisting of:
- Best-in-breed technologies when it comes to IT security that incorporates the all-encompassing scope of AI & ML.
- Curated policies & processes, originating from a strong services & technical team that analyzes how tech is adapted in different customer segments. This gives us a plug & play framework for a holistic understanding of the tools a particular company should adopt and the regulatory bodies that company should comply with.
- Strict adherence to set SLAs, backed by our 180+ tech teams that maintain your critical infrastructure and make recovery times faster than ever.
So, if you’re ready to make ESG a reality, click here to start a crucial new chapter of YOUR growth story!