
Let’s take you back to 2015, when Ukraine was a much calmer place. Relatively, because the seeds of the current war were being planted then itself with Russia’s annexation of Crimea. On one not-so-fine day in December, more than 2.3 lakh Ukrainians suddenly lost access to power for close to 6 hours. Not a big deal in India maybe, a big deal there. Turns out, Russian hackers planted malware into a Ukrainian electric utility company’s infrastructure. And the way they achieved their master plan was through… a simple, seemingly innocuous email sent to a power plant employee.
Around the same time, Google and Facebook realized that they were duped out of $120 million in vendor payments. Nope, it wasn’t an army of hackers perpetually using brute force and DDoS attacks to breach the seemingly impenetrable servers of these tech behemoths. It was a single guy called Evaldas Rimasauskas creating a series of fake invoices over a period of 2 years in the name of Taiwan-based Quanta Computer, one of Google and FB’s actual vendors.
Popular culture dictates that black-hooded cyber criminals’ slave away on their systems all day, trying to find the slightest hint of fallacy. But the fact of the matter is:
“Today’s attackers don’t hack in, they login.”
And they login through a variety of social engineering methods, the most common of which is known as phishing. It’s a type of attack often used to steal user data, like credit card numbers or more relevantly, login credentials, by manipulating the victim to provide details.
Often, the attacker masquerades as a trusted entity and dupes a victim into opening an SMS or an email. Post which, they are tricked into clicking a malicious link and entering their details on said link. The attacker then uses these credentials to enter the system and plant malicious software like malware and ransomware. Or, if they aren’t looking for ransom, they simply extract the info and sell it to the highest bidder.
The ramifications are frightening. Decreased stock performance. Disruption of operations. Damage to your brand image. Loss of customers, assets, and IP. It’s a long, depressing list.
Safe to say that phishing has become a real problem.
- It’s now become a quintessential service on the dark web.
- Over 3.4 billion malicious emails are sent out daily.
- According to a study by Norton, 88% of organizations face spear phishing attacks every year. (More on spear phishing in a bit.)
- India Ransomware Report 2022 calls out phishing as the major pivot point for attackers gaining initial network access.
There are many types of phishing. Fair warning, be prepared for force-fits and oceanic puns.
- Smishing is phishing where the attack is through SMS.
- Vishing is through voice call.
- Spear phishing targets employees in a specific enterprise.
- And whaling is directed at senior executives and other privileged users in that enterprise.
There was a time when there were tell-all signs that you were being phished. Spam mails loaded with typos, sketchy website names, shady messages asking you to change your password WITH IMMEDIATE EFFECT.
But as phishing programs became more and more sophisticated and less and less distinguishable from official communication, along came something to counter it called MFA.
Multi-Factor Authentication. (MFA)
An authentication method requiring users to provide two or more verification factors to gain access to a resource. Essentially, to access something, you need to have 2 of these 3:
- Things you know, like your password
- Things you have, like your smartphone
- Things you are (inherence), like your voice and your fingerprints
The most common MFA is a login on your device, followed by an OTP on your phone. Google does a login, followed by a tap of acknowledgement from a previously used device.
It drove away attackers… for a while. Then, they figured it out and came back. And boy, did they wreak havoc. In recent times, companies like Reddit, Twilio and Uber have all been subjected to MFA bypass attacks. All Uber’s attack involved was an attacker pretending to be IT support, and boom, they were in.
Here’s a (shockingly) easy way that attackers can bypass MFAs:
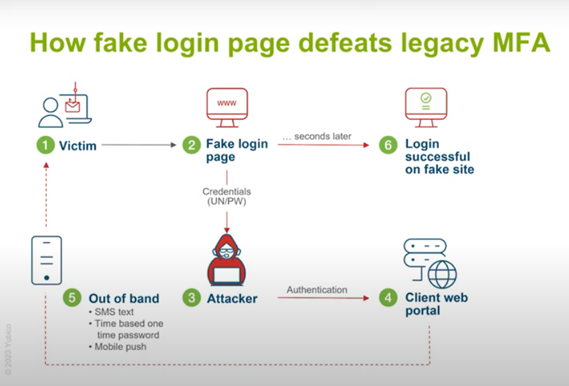
They lure you to a fake login page. You enter your username and password. The attacker now has it and uses it to login to the actual page. You then get an OTP and enter it into what you think is the actual page. Your attacker has that too, and now they’re in.
Truth is, there are many limitations to traditional MFA. Transparent reverse proxies (TRPs) can bypass them. OTP codes are usually 4-6 digits long, and a hacker could use brute force to obtain the right OTP code if your app’s rate limit restriction is ineffective. And if the factor other than your login is not linked to a particular device, like email-based verification, things can go south very fast.
Here’s a comparison of the different types of MFAs from weakest to strongest:
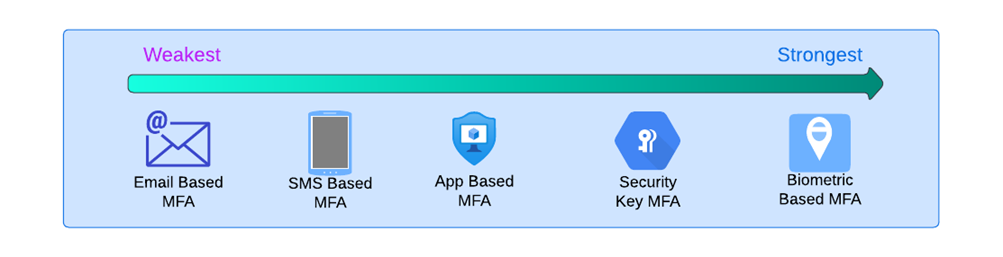
And the solutions towards the right end of this spectrum are exactly what you need to safeguard your organization from phishing. They’re aptly called phishing-resistant MFA.
Resistance is achieved by providing proof of identity combined with intent through deliberate action. And it incorporates something called a FIDO authenticator, named after the alliance, that pioneered it, that uses public key cryptography to ensure utmost security.
Public key cryptography is a method of encrypting data with two different keys – a public key available for everyone to use, and a private key for individual users. The public key encrypts, the private key decrypts. All it takes is an origin ID and token/session banding to ensure secure access. You get a certified physical token, always keep it on you, use it during your login, and that’s that. There are no shared secrets at any point in the login process, eliminating the attacker’s ability to intercept and replay access credentials. Funny enough, even though this type of authentication is only recently gaining prominence, it’s been around for close to a decade.
Let’s now revisit the earlier scenario of an attacker bypassing your OTP-based MFA and replace that with a FIDO-based physical token. Sure, the attacker may have your credentials at the first hurdle, but as soon as they move to the second step, your site will ask for FIDO-based authentication involving cryptographic exchange, and they won’t be able to login. Your site will recognize that the incoming user does not have the token to authenticate, and access is promptly denied.
There are many benefits to adopting phishing-resistant MFA:
- The user experience is smooth, while security is incrementally increased. In the case of FIDO2 authentication, you don’t even need a password.
- It increases security, especially when dealing with outside organizations and active/passive third parties.
- It incorporates more precise controls for access to files, internal networks & other systems.
- It provides a mechanism for organizations to meet security and regulatory requirements.
Sure, it requires some investment, but it also leaves no stone unturned in ensuring completely secure authentication and is your best bet against the perils of phishing. So if this article has made you a believer, and you’re ready to assimilate phishing-resistant MFA into your organization, click here for tips on how to get started!