Digital Infrastructures For Digital India
As India speeds through this phase of rapid digital transformation, cloud has emerged as a preferred choice for enterprises when it comes to setting up supporting digital ecosystems. In today’s complex landscape, the versatility of cloud ticks a lot of boxes when it comes to fulfilling what organizations have to be cognizant of during this time:
- On one side, business moves at an exponential pace, organizations require agility and scalability in their systems to keep up with the growing business demand – something ticked off by various public clouds available in the market.
- On the other, data localization requirements increase through new & upcoming regulations like DPDPA, organizations need tighter control of mission-critical workloads – something ticked off by private & on-premises clouds.
Hybrid Cloud: The Balance Enterprises Seek
The beauty of the sheer scope of clouds available in today’s market is that you can mix & match them based on your organization’s needs. That’s why many enterprises today are opting for hybrid clouds that balance the scalability of public clouds with the control & compliance benefits of private & on-premises clouds. In fact, according to NASSCOM, 60% of Indian enterprises have already started incorporating hybrid multicloud systems in their organization.
The main methodology behind hybrid cloud – of putting each organizational workflow into its ideal IT environment – is a highly enticing one for organizations seeking optimization. In addition to the agility-compliance balance it helps enterprises achieve, there are many other reasons behind why many are going with hybrid cloud as the ideal environment for them:
- The practice of ideal environments provides high levels of cost optimization.
- The distributed workloads improve uptime, uplifting customer experience.
- Using multiple clouds primes up a business for effective disaster recovery & continuity.
- The variety of options gives tech flexibility and avoids vendor lock-in.
More Environments, More Complexity
However, enterprises are increasingly finding out that more environments could lead to more complexities – a precarious situation that malicious attackers are trying to exploit. In fact, cyberattacks on cloud infrastructure in India rose by 70% YoY – a major part of why India is now the second most hacked nation in the world.
Using advanced tactics, cyberattackers are being increasingly successful when it comes to finding cloud blind spots in an organization’s infrastructure.
Today’s Top 5 Cloud Blind Spots
With cloud complexities growing and organizations struggling to maintain control, attackers are finding their way in through these 5 preferred vulnerabilities:
1. Cloud Misconfigurations
65% of cloud breaches are linked to misconfigurations, with nearly 9% of Indian cloud storage buckets containing restricted or confidential data. That means millions of records that attackers can exploit instantly.
Simple errors when setting up clouds, like leaving storage buckets public or mismanaging IAM roles, can create massive vulnerabilities that often end up being the primary cause of many cloud-based intrusions.
2. Embedded Secrets in Cloud Workloads
77% of organizations found hardcoded secrets in production apps
Hardcoded credentials, API keys and tokens inside applications or IaC scripts act as hidden backdoors for attackers. Once exposed, they can provide unrestricted access to critical systems and data.
3. Shadow IT
Nearly 80% of employees admit to using unauthorized SaaS apps at work
Employees often adopt unsanctioned SaaS apps & cloud services to boost productivity without IT approval. These “invisible” tools bypass governance, compliance and security monitoring, creating blind spots.
4. Insufficient Cloud Encryption & Data Protection
Only 40% of Indian enterprises encrypt sensitive cloud data by default
Many organizations fail to apply strong encryption by default to sensitive workloads in the cloud. This leaves customer data, intellectual property and financial records vulnerable in storage and transit.
5. The Gap Between Cloud Complexity & Security Governance
72% of CISOs cite overwhelming cloud complexity as their top challenge
As hybrid and multicloud environments expand, managing identities, policies and compliance across platforms becomes a huge challenge. This governance lag creates cracks in the security fabric that attackers can easily exploit.
To combat this growing threat, for these 5 vulnerabilities and all others, you need a partner that can provide end-to-end protection across your entire hybrid cloud infrastructure.
Secure Your Entire Hybrid Cloud With Tenable’s CNAPP Capabilities
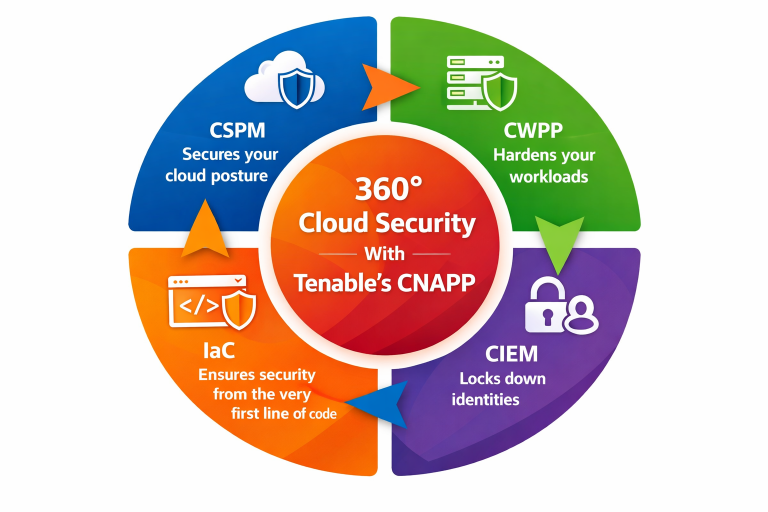
Tenable, the world’s #1 vulnerability management platform, offers an industry-leading Cloud Native App Protection Platform (CNAPP) that delivers end-to-end visibility, risk prioritization and proactive defense for hybrid & multicloud infrastructures. The platform combines 4 essential cloud security services into one holistic, easy-to-use platform:
The Core Components of Tenable’s CNAPP Solution | |||
Cloud Security Posture Management (CSPM)
Our CSPM continuously scans cloud environments for misconfigurations, compliance violations and risky settings – preventing issues like exposed storage buckets, weak IAM policies or missing encryption before attackers exploit them. | Cloud Workload Protection Platform (CWPP)
Our CWPP provides runtime protection, vulnerability scanning & threat detection to secure workloads in dev & production – providing holistic protection across VMs, containers, server workloads and the rest of your hybrid cloud. | Cloud Infrastructure Entitlement Management (CIEM) Our CIEM monitors human & machine identities in the cloud – detecting overprivileged users, risky entitlements and suspicious access patterns. This is particularly critical in India, where identity breaches are a top attack vector. | Infrastructure-as-Code (IaC) Security
Our IaC security frameworks inculcate security by design into every aspect of production – preventing insecure configurations from appearing at any point in the production cycle. |
Close Your Blind Spots With Our CNAPP’s Shared, Superior Capabilities
Tenable’s CNAPP integrates all its tools seamlessly to provide your organization with the capabilities to eradicate all the cloud blind spots attackers usually exploit:
Top Blind Spots | How Tenable’s CNAPP Eradicates Them |
Cloud Misconfigurations |
|
Embedded Secrets in Cloud Workloads |
|
Shadow IT |
|
Insufficient Cloud Encryption & Data Protection |
|
The Gap Between Cloud Complexity & Security Governance |
|
With Tenable’s CNAPP, you stay agile, secure and compliant across your entire hybrid cloud at all times – click here to speak to an iValue-Tenable security expert today about how to secure your entire cloud infrastructure.
