Embedded Systems Pose A Different Kind Of Threat
Last year, India had to deal with heightened geopolitical tensions that made it the target of several adversarial nation-state hacker groups. Massive volumes of attacks were directed at our critical infrastructure in the aftermath of Operation Sindoor, and the spillover has continued in 2026.
Industries like defense, power, healthcare and transportation are becoming increasingly preferred targets for these groups because of the potential to severely destabilize the country, should their attempts be successful. What these types of industries also have in common is a mix of traditional IT and embedded systems in their IT infrastructure.
Embedded systems are hardware-firmware compute components that directly sense, control, automate or protect cyber-physical processes. If compromised, breaches could have direct physical consequences, whether its:
- Adversarial control of defense weapons systems
- Blocking of telecom networks by taking over firmware in towers
- Electrical shutdowns through breaches in power plant machine controllers
Embedded systems face different kinds of threats when compared to traditional IT systems – yet, for the longest time, there wasn’t an effective cybersecurity framework to help enterprises combat them. Efforts to create one in 2020 highlighted a significant gap in existing resources, with earlier frameworks lacking the nuanced understanding required to address the unique vulnerabilities inherent in these systems. A framework needed to be introduced for today’s embedded devices that:
- Connect to enterprise networks
- Handle sensitive data
- Control physical processes
- Cannot be easily replaced or patched
That was accomplished earlier this year, when MITRE – an organization famed for their ATT&CK and D3FEND frameworks – introduced the Embedded Systems Threat Matrix (ESTM) 3.0 in association with the US Air Force’s Cyber Resilience Office For Weapons Systems (CROWS). While the framework was designed to protect embedded systems that underpin defense technology in the US, its principles very much extended to India and so many of its critical infrastructure sectors.
What’s New In ESTM 3.0?
While the first two versions of ESTM were more iterative in nature, 3.0 is more of a formal framework that prioritizes 3 key areas of improvement:
- It emphasizes system-agnostic tactics and techniques that ensure the framework’s applicability across diverse domains, making it highly relevant for various Indian critical infrastructure sectors.
- Its structure is aligned with Structured Threat Information Expression 2.1 – an integration that promotes interoperability and enables machine-readable threat intelligence.
- Finally, it focuses on developing and validating attack patterns specific to embedded systems, providing cybersecurity teams with actionable insights to strengthen their security posture.
ESTM 3.0 uses MITRE ATT&CK as a starting point to map specific tactics & techniques, yet it’s important to acknowledge that both frameworks are for vastly different systems:
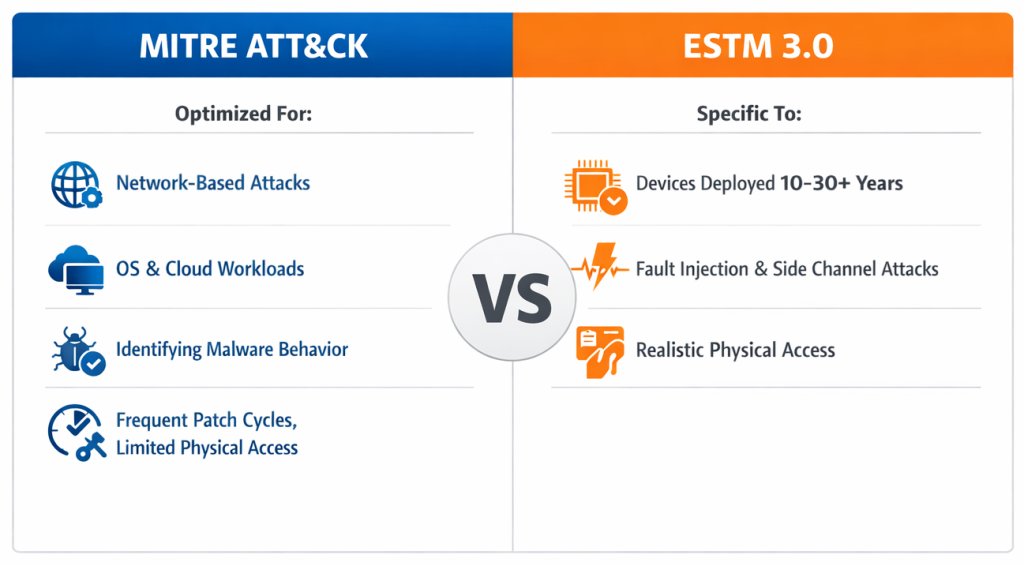
While ATT&CK applies to traditional IT that lives in clean software boundaries, ESTM 3.0 focuses more on securing real devices (IoT, industrial controllers, vehicles, medical equipment) where hardware, firmware and physical access are essential parts of daily environments.
Combining Specific Techniques With Superior Threat Modeling
ESTM 3.0 is derived from the robust structure of MITRE ATT&CK yet tailored to the unique characteristics of embedded environments. These are some of the categories when it comes to attacker tactics:
Reconnaissance When they actively or passively gather information that can be used to support targeting a specific embedded system or component. | Initial Access When they are trying to gain access into embedded systems or components. |
Execution When they try to run malicious code. | Persistence When they try to maintain a foothold on these systems. |
Privilege Escalation When they try to gain higher level permissions. | Defense Evasion When they are trying to avoid being detected. |
Credential Access When they are trying to steal credentials. | Discovery When they try to map out environments of embedded systems and components. |
Lateral Movement When they are trying to move through environments using these components. | Collection When they are trying to gather data of interest for these systems. |
C&C When they are trying to command and control a compromised system. | Exfiltration When they are trying to steal data through these embedded systems. |
Impact When they are trying to manipulate, intercept or destroy your systems and data. | |
This forms the basis for teams to undertake superior embedded attack path analysis. In particular, ESTM 3.0 is highly effective in combining these tactics and simulating multi-stage attacks like the following:
Physical Access 


A Powerful Tool Against Emerging Embedded Systems Threats
With ESTM 3.0 now available for enterprises to integrate, teams can now model different kinds of advanced threats for both hardware and firmware components in embedded environments:
ESTM 3.0 Helps You Stay Prepared For Emerging | |
Hardware-Based Attacks | Firmware-Based Attacks |
|
|
ESTM 3.0-Fortified Security Stacks By iValue
ESTM lays out a framework that helps secure vital embedded systems in areas like:
- Transportation (air, space, maritime, autonomous, military)
- Energy
- Healthcare
- Industrial Processes
- Sectors that heavily utilize robotics
One of the reasons why iValue is considered the preferred managed tech partner for many enterprises across the country is our ability to create personalized security stacks specific to your industry and individual requirements. All our critical infrastructure stacks (Manufacturing, Healthcare, Smart Cities, etc.) now incorporate ESTM 3.0 to create blended, holistic security across both traditional IT environments and embedded systems.
A crucial gap has now been plugged with the introduction of ESTM 3.0, and now, organizations in India’s critical infrastructure can achieve comprehensive cybersecurity that defends against breaches across all environments. Click here to start securing your enterprise today.
