Ever Under Attack?
Reach Out the Moment You’re Under Threat
Whether it’s ransomware, DDoS, or a data breach—our incident response team is ready to step in.
Why “Under Attack” Matters
Act Fast. Stop the Damage Before It Spreads
Cyberattacks on Indian enterprises have grown in scale and sophistication—DDoS blasts, ransomware lockdowns, phishing waves, identity breaches, and more.
No industry is immune: from BFSI and healthcare to manufacturing and critical infrastructure.
When your systems falter, the fallout can include:
- Operational disruption that halts revenue streams
- Financial losses from ransom demands or theft
- Reputational damage that erodes customer trust
- Regulatory fines for missed reporting deadlines
What We Deliver
A Complete Response—from Detection to Recovery
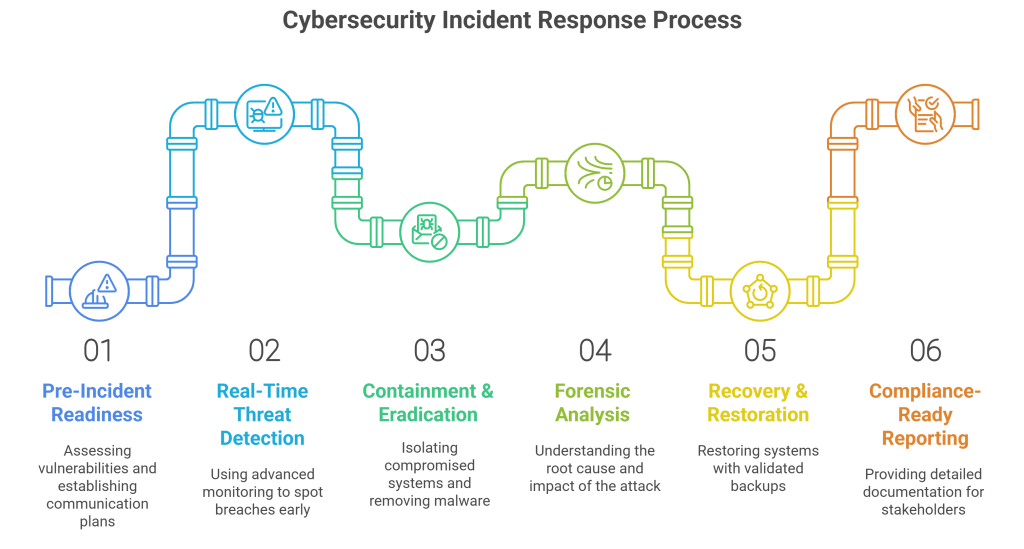
Built for the Real World
We Align People, Process, and Technology to Protect What Matters
We combine deep cybersecurity expertise, strategic technology partnerships, and domain-specific threat intelligence to guide organizations through the full IR lifecycle. Whether you’re in BFSI, healthcare, manufacturing, or critical infrastructure, iValue tailors IR strategies to your risk landscape.
- 24×7 IR Support
- Customizable IR Playbooks
- Regulatory & Compliance Alignment
- Integration with Existing Security Tools (SIEM, SOAR, EDR)

Get Started Now!
If you’ve ever felt under siege, iValue’s IR experts stand ready to help you prepare, detect, contain, and recover—while ticking every regulatory box.
Latest Resources

Strengthening Data Protection to Meet SEBI’s Encryption Mandates
Introduction to SEBI’s Encryption Mandates India’s financial markets are currently in a supercharged state. With increasing participation from retail investors, the National Stock Exchange (NSE) reported daily trading volumes averaging

Leveraging the MITRE ATT&CK Framework for Enterprise-Wide Cybersecurity Posture Management
Overview of the MITRE ATT&CK Framework If your security doesn’t have precision and perfection, you’re sure to miss out on threats that sneak in. The MITRE ATT&CK Framework gives your

Key Challenges in Implementing SEBI’s New Cyber Security Guidelines
Technical Challenges in SEBI Cybersecurity Implementation: Encryption, SOCs, and Tool Integration The SEBI guidelines have been crafted to focus on resilience which is captured in the title ‘Cyber Security
