As India rapidly continues on its digital transformation journey in 2026, the cyber landscape surrounding it sees a clear duality – it has become both a catalyst for progress and a vector of profound risk. This is especially amplified in the world of cybersecurity – according to WEF’s ‘Global Cybersecurity Outlook 2026’, accelerating technological change and persistent geopolitical volatility is leading to increasingly widening capability gaps for Indian enterprises when it comes to securing their digital infrastructures.
These gaps come at an extremely heightened time. The country faced over 265 million cyberattacks last year, according to Seqrite’s India Cyber Threat Report. The scenario requires Indian enterprises to be extremely vigilant – any gap at any given point in time could lead to a breach that causes massive financial, operational and reputational damage to your organization.
So, with a new year that brings new types of risk, how can we bridge this cybersecurity capability gap to stay ahead of emerging threats?
3 key drivers are behind the gap we see today, and iValue can help you overcome all of them with our India-optimized, enterprise-specific managed services.
Driver # 1: AI Advancements
Most industries are being transformed by AI, and cybersecurity is no different. According to World Economic Forum report, 94% of respondents say that it will be the most significant driver of change in 2026. AI is reshaping the cybersecurity landscape through three interconnected elements:
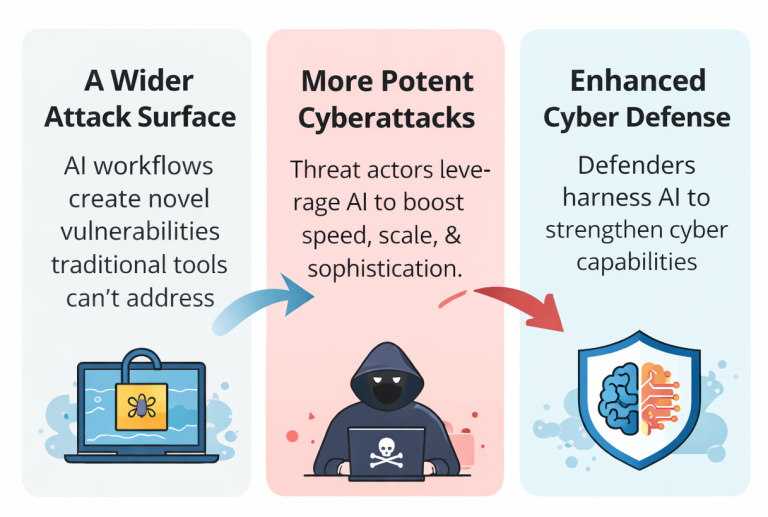
The gap in this scenario comes from organizations unable to leverage AI for cybersecurity purposes because of the complexities that come with it. 54% of respondents identified limited knowledge and skills as a key obstacle to adopting AI-driven solutions for cybersecurity.
So, how does your organization start integrating these potentially transformative tools into your cybersecurity strategies without any friction?
We at iValue believe this process starts right at a ground level, with clean, governed data that helps AI programs become more accurate in their decision-making. Once those roots are established, you can use AI in a variety of ways to arm your cybersecurity, ranging from:
- Real-time anomaly and vulnerability detection through complete visibility of your networks
- Incident response through automated playbooks that cut response times to seconds
- Comprehensive forensic investigations of incidents through superior ML-led analytical prowess
Driver # 2: Increasingly Interconnected Supply Chains
In a world driven by outsourcing, very few organizations develop everything in-house. Whether it’s adopting AI into processes, migrating to cloud or gaining insights from organizational data, Indian enterprises now depend on specialised third parties to carry out these tasks – so that they can continue to focus on their core competencies.
It leads to an ever-expanding, highly-linked supply chain – where a single incident halfway around the world can have global ramifications and gravely impact organizations like yours. Even if you have strong internal controls in place, your weakest link (and a way for attackers to get in) could be a supplier or partner with lower cybersecurity maturity.
The gap here comes from not having enough initiatives in place to deal with this greatly expanded attack radius. Only 27% simulate cyber incidents or conduct recovery exercises, while 33% comprehensively map supply chain ecosystems to gain a deeper understanding of cyberthreat exposures & limitations.
These are the top 3 supply chain risks, according to WEF:
- Inheritance Risk: The inability to assure integrity of your third-party software, hardware & services.
- Visibility Risk: The lack of visibility into your extended supply chains.
- Concentration Risk: Having too great a dependence on certain critical supply-chain partners.
To close this gap, you need to set in place several mechanisms that permeate throughout the supply chain lifecycle:
Inventory
Every supplier comes with certain dependencies that you need to be aware of right at the outset. iValue recommends integrating a Runtime Bill Of Materials (RBOM) for all your supply chain relationships. This gives you a running inventory of what’s going on in all your live environments. | Controls
Suppliers will be dealing with a lot of your sensitive data. Therefore, at the time of contract signing, it is very important for your enterprise to add SLAs for your suppliers, mandating them to integrate the best methods of data security when it comes to safeguarding your sensitive data. | Monitoring
Integrating SLAs is one thing – it is essential to ensure your suppliers always adhere to them. Periodic reviews are beneficial, but the best option is to leverage automation in order to continuously monitor their systems for any threats and anomalies. | Continuity
It’s important to pray for the best and expect the worst. Scenario-based testing helps prime your supply chain ecosystem against emerging threats, while business continuity programs ensure that your systems get minimally impacted and stay up-and-running in the event of a supply chain breach. |
Driver # 3: Growing Cybersecurity Skills Shortage
The first two drivers (AI & supply chains) speak to an exponential expansion of cyber risk. However, the biggest reason for the cybersecurity gap today is an acute shortage in cyber skills to deal with this expanded risk. 43% of regional organizations surveyed in the WEF report say they are internally missing critical people & skills. These are the top 3 cybersecurity roles experiencing worldwide shortages, with all of them critical in maintaining a proactive cybersecurity posture:
- Threat Intelligence Analysts
- DevSecOps Engineers
- IAM Specialists
In this scenario, it could take months for you to get someone qualified in the roles you’re seeking – meanwhile, attackers evolve their strategies on a weekly, even daily, basis. It is for this reason that enterprises are increasingly preferring to go with managed cybersecurity service providers (like iValue) to fortify their cybersecurity up to the levels demanded by the 2026 attack landscape.
Stay Cyber Resilient in 2026 with iValue
iValue is a preferred choice for many Indian enterprises not because we invent new tech. Instead, we take best-in-breed cybersecurity solutions from around the world and curate them for your specific enterprise requirements. iValue plugs in all the gaps seen in today’s cybersecurity scenario through:
- Intelligent technologies that bring best-in-class AI capabilities to arm your cybersecurity defence, with comprehensive governance of your AI workflows
- Continuous monitoring across all your supply chain relationships, with scenario-based testing to stay ahead of emerging threats
- Unparalleled expertise when it comes to cybersecurity in India, with 24×7 support whenever you need it.
Yet, ultimately, the scenario requires you to move beyond closing gaps. It demands a move from cybersecurity to cyber resilience – a truly proactive security posture that will prepare you for anything 2026 brings. Here’s what WEF deems as the top challenges to strengthening cyber resilience – and how iValue solves for them:
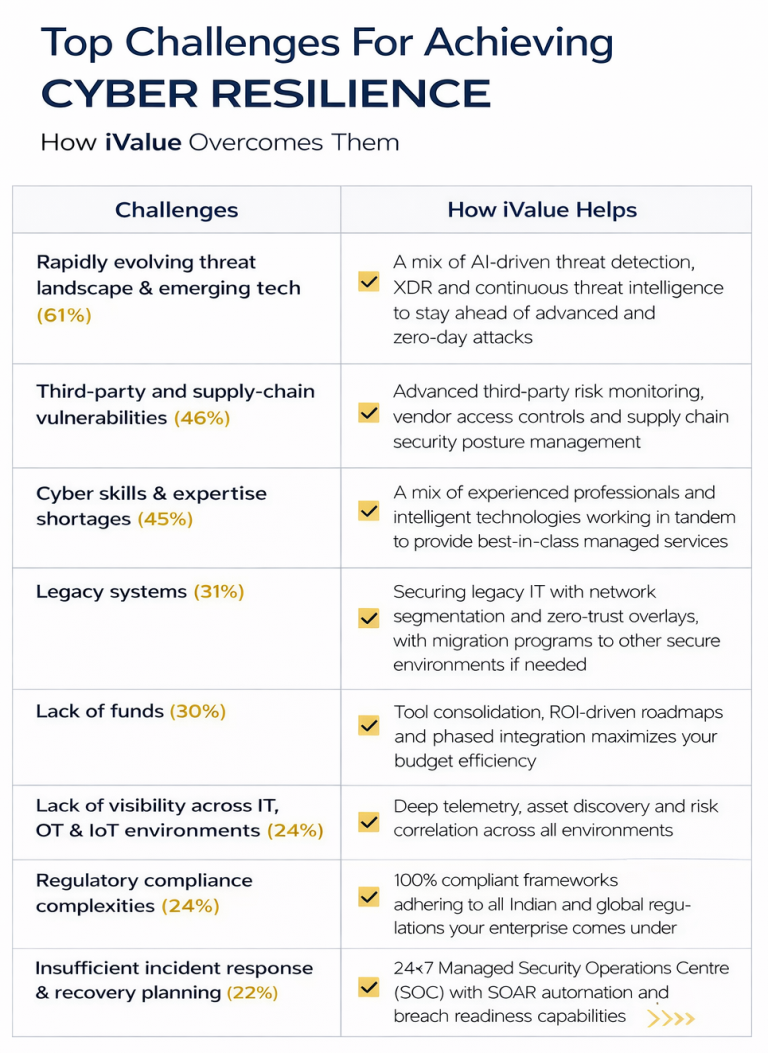
If you feel any (or all) of these are current challenges for your enterprise, speak to an iValue expert on how you start becoming cyber resilient for 2026.
