- Home
- /
- Custom IT Solutions for...
- /
- Work From Home Solutions
Solutions
WORK FROME HOME SOLUTIONS
The world is facing a global lockdown due to the COVID-19 outbreak. In response to this evolving pandemic, most organisations have initiated (or are being encouraged to implement) work from home plans for their employees to keep the business running, while practicing social distancing to limit the spread of the virus.
At iValue, we understand that working from home may be a sudden transition for your organisation, as well as your employees. Your business processes will need to be updated to support your work from home plans. And the work environment of your employees need to be optimised and secured as well. Moreover, you will need solutions that improve your team’s productivity while driving the overall profitability of your business.
To this effect, iValue introduces the Work from Home Solutions to support your organisation’s work from home needs. Our solutions are designed to optimise your team’s productivity while working securely from home.
How can iValue Help you?
You need a trusted partner who can help you navigate and choose the right solution from the plethora of options available right now. iValue can do that for you.
With our experience and expertise in providing solutions and services, we can help you adopt a powerful and secure Work from Home solution for your employees, based on the specific needs of your organisation.
Our goal is to manage time efficiently in this adoption process, and focus on boosting your team’s productivity while working from home. We start by understanding the objectives, and studying your IT landscape and security policies. Based on that, we recommend solutions and services that will fulfil our goals.
Take a look at our solutions and services listed below.
SOLUTIONS
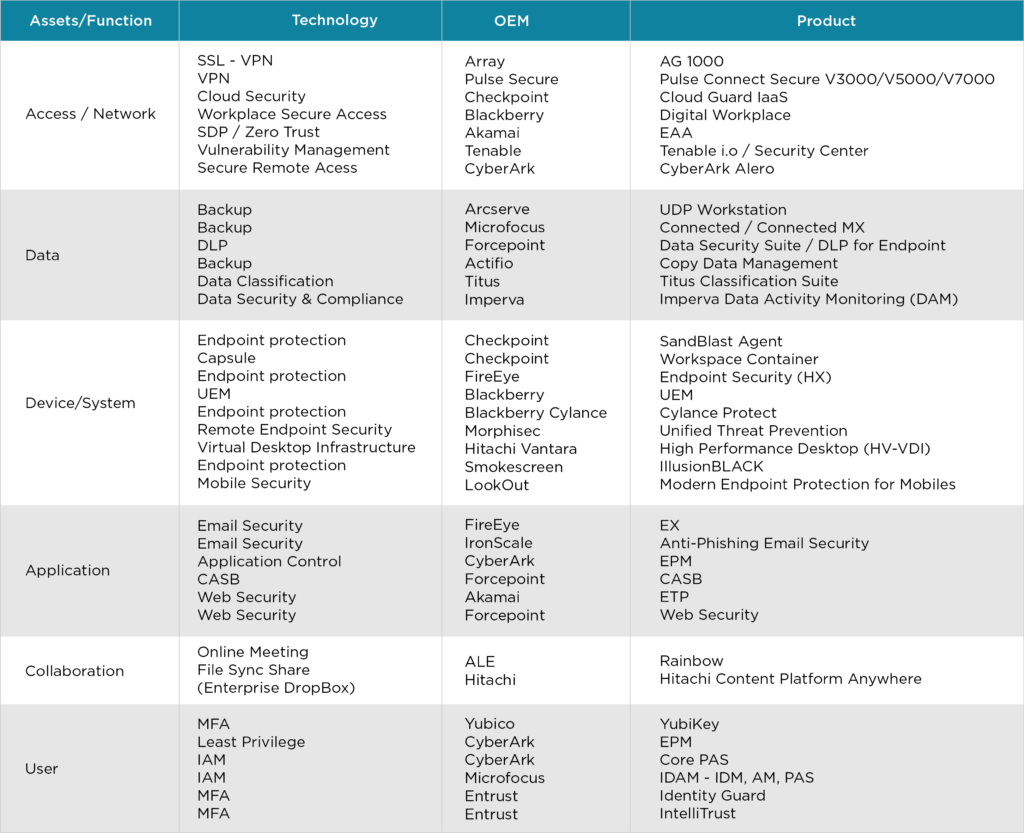
Unified Threat Prevention
Unified Threat Management (UTM) solution is a single, low cost, and easy-to-manage appliance that can replace multiple security software products running on separate servers. It offers an irresistible value proposition for smaller organizations and branch offices by securing devices and protecting users from security threats in a simplified manner.
Multi-Factor Authentication
Multi-Factor Authentication solution enables users to gain access only after successfully presenting two or more pieces of evidence to an authentication mechanism. Two factor authentication – USB Based & Phone-based authentication with SMS and real-time number verification – provides the ideal mix of convenience, security, and low cost that helps a company with service activation, enable secured access to the mobile workforce, and verify financial transactions.
Unified Threat Prevention
Unified Threat Management (UTM) solution is a single, low cost, and easy-to-manage appliance that can replace multiple security software products running on separate servers. It offers an irresistible value proposition for smaller organizations and branch offices by securing devices and protecting users from security threats in a simplified manner.
Multi-Factor Authentication
Multi-Factor Authentication solution enables users to gain access only after successfully presenting two or more pieces of evidence to an authentication mechanism. Two factor authentication – USB Based & Phone-based authentication with SMS and real-time number verification – provides the ideal mix of convenience, security, and low cost that helps a company with service activation, enable secured access to the mobile workforce, and verify financial transactions.
Cloud-based Communication
Cloud-based communication models run network and applications from the cloud, thus guaranteeing better user experience for your employees. It offers faster deployment and quicker adoption. With such models, you have access to the latest software and releases, with more control on security and user management.
Virtual Secure Access Gateway
Virtual secure access gateways enable secure access to applications, desktops, files, networks and websites for your work from home employees. This provides secure connectivity, end-point and server-side security and application-level AAA policies on a per-user basis.
Secure Remote Access
Secure remote access protocols prevent unauthorised access to your network and sensitive data. WIth this solution, you activate secure connections to apps and files across different operating systems and devices for your employees working remotely. With security in place, your employees can focus on working efficiently.
Secure VPN
A secure virtual private network, or SSL VPN, establishes an encrypted data tunnel for data to travel from one location to another on the internet. It lets remote users access Web applications, client-server apps, and internal network utilities. The SSL VPN can consist of one or more VPN devices, and the network is encrypted with SSL or TLS protocol.
Remote Access VPN
Remote access virtual private network, or remote access VPN allows your employees to securely and privately access data on a remote network. It creates a secure virtual tunnel between an offsite employee’s device and the company’s network. This helps your employee connect to all your company resources without compromising data security.
Mobile Security
Our mobile security solution protects your portable devices – laptops, tablets, smart watches, phones – against cyber threats. It also refers to the means by which a mobile device can authenticate users and protect or restrict access to data stored on the device. Authentication methods include passwords, personal identification numbers (PINs), and pattern screen locks. More advanced forms of authentication include fingerprint readers, eye scanners and other forms of biometric readers.
Endpoint Security
Endpoint security secures and protects endpoints, or end-user devices like desktops, laptops, and mobile devices connected to a remote network, against zero-day exploits, attacks, and inadvertent data leakage resulting from human error. It covers your entire network and protects against different types of security attacks, while antivirus software covers a single endpoint and only detects and blocks malicious files
SERVICES
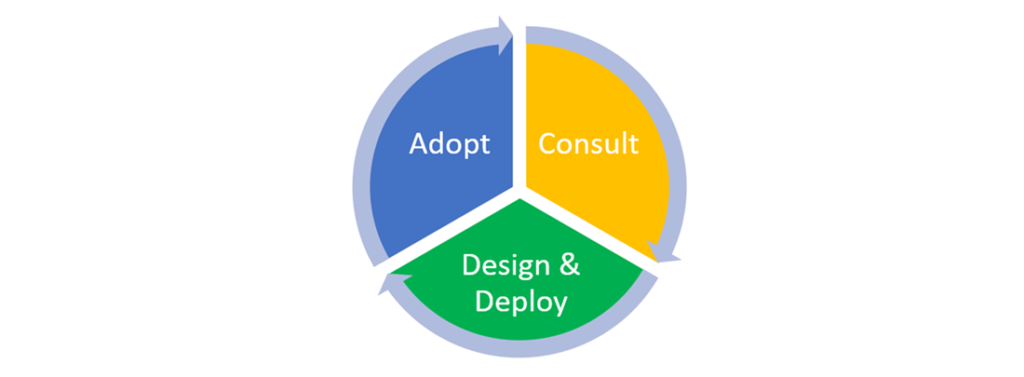
Consultancy Services
With plethora of solutions available for Work From Home solution, you need to have a trusted partner who can help you navigate and help you choose the right solution. With experience and expertise in providing solution and services, iValue can help customers to choose the right “Work From Home” solution for employees meeting the needs of the organization. By understanding the objectives, studying the IT landscape and security policies of the customer our consultant will recommend you the right solution for quicker adoption as time is the essence and productivity of employees matter.
Design and Deploy Services
With our experience and expertise, iValue helps customers to design and deploy the “Work From Home” solution as per industry best practices and requirements of the organization taking care of optimal user experience. Remote Deployment services are available.
Adoption Services
iValue understands that needs evolve and infrastructure goes through changes after initial deployment. For better value realization of investment, with our adoption services, customer can get insight on using additional features of the solution purchased.
WORK FROM HOME OFFERINGS