Do you think your organization is 100% safe with just MFA? Think again! Back in 2023, despite having MFA protocols in place, MGM Resorts reported a massive $100 million in damages as attackers used stolen Okta credentials to social engineer their approach through MFA. It led to one of the biggest cyber-attacks in the hospitality industry.
To make matters worse, Gartner predicts that within the next two years, AI agents will cut down the time taken to misuse account exposures by 50%, making it even easier for attackers to bypass authentication controls – including MFA.
It’s not easy to admit that despite MFA adoption skyrocketing, there is a blind spot in overall security posture. While CXOs shift their focus to guarding the ‘entrance’ to an organisation, the monitoring of those who have already entered is often forgotten. In fact, if your cybersecurity strategy still stops with the login screen, you’re leaving your organisation wide open to threats that are evolving faster than the speed of light.
Evolving Modern Day Threat Landscapes
Cyber criminals today aren’t just releasing their arrow and hoping it hits the target. They’re far more advanced, their technology futuristic, and their approach calculated. They don’t just steal passwords, they’ve understood that the real objects of value are hidden behind authenticated barriers, in collaboration tools, and cloud environments.
Today’s attackers get you from within your organisation’s authenticated landscape itself:
- Collaboration platforms: Compromising your Teams, Slack, or Google Workspace accounts can let perpetrators launch attacks using trusted sources, thereby also exploiting colleague relationships and shared access permissions.
- Post-delivery malware: Bypassing traditional email security that only scans the overall perimeter, malicious files can be sent through legitimate channels after authentication.
- Lateral movement: Exploiting your API connections and third-party integrations to access broader systems and data repositories, attackers can move laterally with ease.
- Zero-day exploitation: Providing attack vectors that can’t be detected by traditional signature-based security, collaboration tools enable unknown vulnerabilities.
- Insider threat amplification: Social engineering, account compromising, and malicious intentions even within trusted collaboration environments weaponizes legitimate user access.
- Data exfiltration: Routine file sharing, document collaboration, and communication patterns that seem to be legitimate to monitoring systems end up being stolen by criminals.
The ecosystem of collaboration tools itself has become a new platform for attackers to take advantage. Teams relying on these platforms for strategizing, customer data transferring, and financial reporting among other internal tasks end up being vulnerable to potential exposure. Archaic legacy systems are built only for perimeter defence, and they are generally unable to keep up with threats that suddenly emerge from within authenticated sessions.
It gets even more complex for legacy systems when zero-day attacks come into play. They don’t match existing signatures and this lets them slip past the basic defence lines. Attack timelines have shrunk drastically too, where what used to take weeks now happens in hours. Is your organisation ready to defeat unknown enemies?
The Limits of MFA (Including YubiKey Alone)
The adoption of MFA worldwide has been impressive, and YubiKey is considered the gold standard in phishing-resistant authentication. Yubico’s hardware-based approach has proven to be effective against credential-based attacks, through an authentication barrier that remote attackers can’t overcome with traditional approaches.
But even the strongest authentication solution has some limitations when it’s deployed in isolation. YubiKey’s strength lies in its identity verification that gives the right person the access to systems. However, authentication is only the first step on the journey to total security.
Your organisation’s legitimate users can successfully authenticate themselves with their YubiKey, but that doesn’t mean that the YubiKey can detect or block malware that arrives through legitimate channels after the login procedure is completed.
For example, a malicious file attachment that is shared through authenticated and ‘secure’ Microsoft Teams accounts or compromised colleague conversations that include dangerous links on Slack channels: These instances can neither be detected or prevented with YubiKey or any other authentication platform.
Device security becomes the critical gap here: Where YubiKey (authentication applications and platforms) ask ‘who are you’ but not ‘what are you doing here’ or ‘should you be here’. At a time like now, the most critical attacks occur after authentication, and this gap becomes extremely crucial.
The Power of Bundling: YubiKey + Check Point Harmony
It’s always been a point of contention as to whether best-of-breed point solutions are better or integrated platforms. However, when it comes to YubiKey and Check Point Harmony, it is easy to see that a combination of the two is the most practical and secure solution for any organisation.
Security Feature | YubiKey | Check Point Harmony | Integrated Solution |
Identity Verification | Hardware-based MFA | Software-based only | Bulletproof authentication |
Post-Login Protection | No coverage | Real-time monitoring | Continuous threat detection |
Collaboration Security | Authentication only | Content analysis | Complete platform protection |
Endpoint Defence | No device security | Advanced threat prevention | Device + identity assurance |
Zero Trust Alignment | Partial (identity only) | Partial (behaviour only) | Complete architecture |
Threat Response | Prevention only | Detection + remediation | Prevention + rapid response |
The partnership between the two gives you comprehensive protection, eliminates blind spots, and address the full spectrum of modern day threats. You get bulletproof identity validation with YubiKey and protection that goes beyond authentication boundaries with Check Point Harmony.
YubiKey’s identity validation layer gives you the foundation for all other security decisions that you can add on. Hardware-based authentication creates cryptographic proof of user identity, enabling sophisticated security policies and risk-based decision making throughout user sessions.
You get added protection with AI-powered threat detection. This system also analyses behaviour patterns to predict and act in advance before new attacks happen, rather than just waiting around for known threat signatures.
Post-delivery remediation brings unique value that traditional security solutions struggle to address. If threats are detected within collaboration platforms, Check Point Harmony automatically quarantines malicious content, revokes access to compromised resources, and alerts security teams. Rapid responses like this shrink the attacker’s opportunity window.
Zero Trust adds another layer of safety by addressing fundamental network security and user behaviour. Instead of simply trusting users based on network locations or initial authentications, the platform continuously validates access decisions based on current contexts, behavioural patterns, and risk indicators.
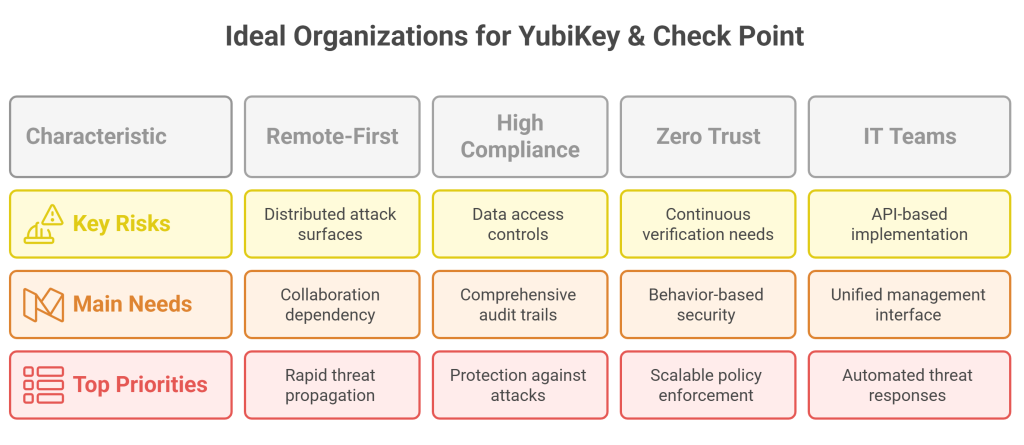
When your threats are modern, why should your security measures be old-fashioned? So a single solution – regardless of quality – cannot offer the comprehensive protection that your organisation needs. If your organisation is part of the above list, you definitely need to rethink any archaic approaches to cyber security. YubiKey’s perfect authentication capabilities form a great basement to the security posture, but you need to balance it out with the top level protection that comes with Check Point Harmony’s full-spectrum threat addressing.
If your organisation recognises this evolution quickly and adapts to the futuristic security strategy that comes with it, you will find yourself better positioned against even the most evolved attacks. Relying on authentication alone may lead organisations to go through financial losses, reputational damage, and even legal repercussions through compliance failure. Stop the blind spots today and prepare to secure your organisation with authentication and post-login protection.
Stop Phishing at the Entry Point
With YubiKey + Checkpoint Harmony, you secure the full spectrum of user interaction: YubiKey delivers phishing-resistant, passwordless login—trusted by governments and Fortune 500s. Harmony Email & Collaboration detects and remediates cloud threats across Microsoft 365, Google Workspace, Teams, Slack, and more.
Built for the cloud. Designed for compliance. Delivered by iValue.
