India has been under attack in 2025 – both on-ground & online. During the time period of the Pahalgam attack and Operation Sindoor, the country’s essential systems faced high volumes of state-sponsored cyberattacks from groups backed by adversarial nations. Many outfits have been involved, yet the flag-bearers of these attacks are Pakistan-backed APT36, also known as the ‘Transparent Tribe’.
APT36 have spent most of the year trying to cripple India’s critical infrastructure:
- Back in March, before the Pahalgam attack, they spoofed the India Post website to infect Indian Windows & Android users with malware.
- Immediately following the Pahalgam attack in late April, the group launched a sophisticated phishing campaign aimed at infiltrating India’s defence networks. Exploiting the heightened emotions at that time was their way of building trust & urgency, and they used tactics like deploying credential-harvesting RATs, screenshot capture and keystroke logging to gain access.
- Then, between May 7-10, they coordinated with 35 other hacktivist groups to launch an all-out offensive, launching over 15 lakh cyberattacks at India’s critical infrastructure (with 150+ being successful) and executing over 650 confirmed DDoS & defacement events.
- They were back at it again in June, with a credential-stealing campaign that involved mimicking NIC documents.
It seems like they’re not stopping anytime soon, and there’s a chance they may amp it up even further. As an Indian organization, you have to be wholly prepared for their attacks.
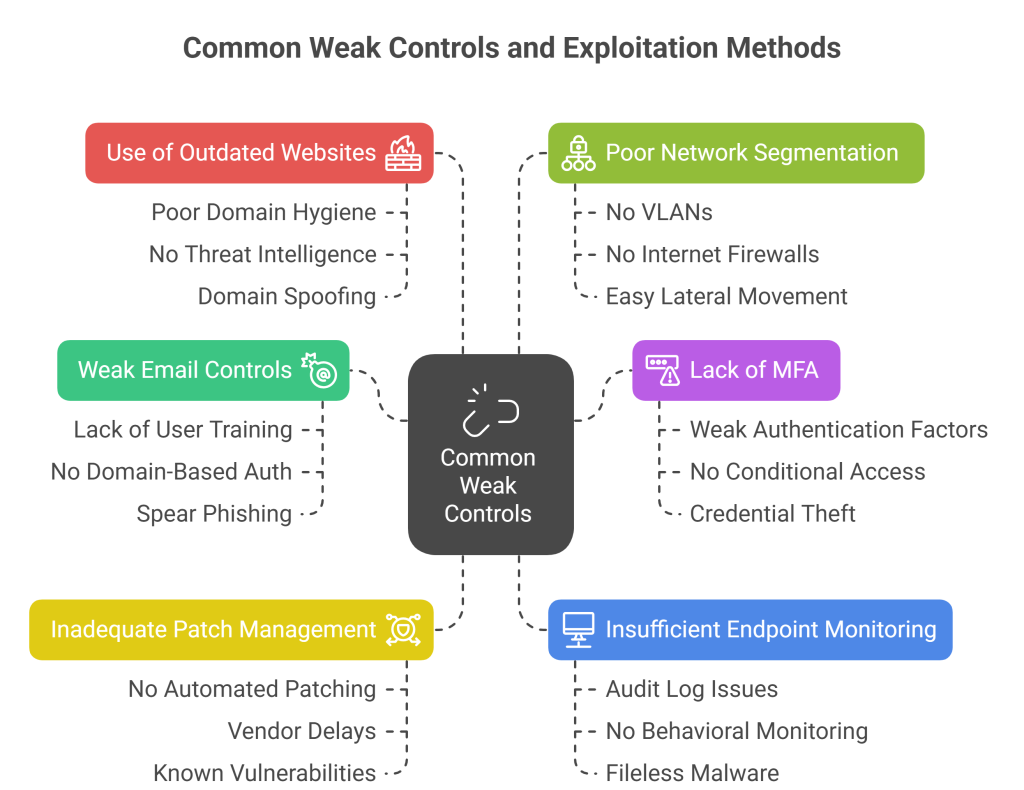
The Controls Attackers Try To Control
Groups like APT36 are known to use long-term, persistent tactics targeted at an organization’s weakest security controls:
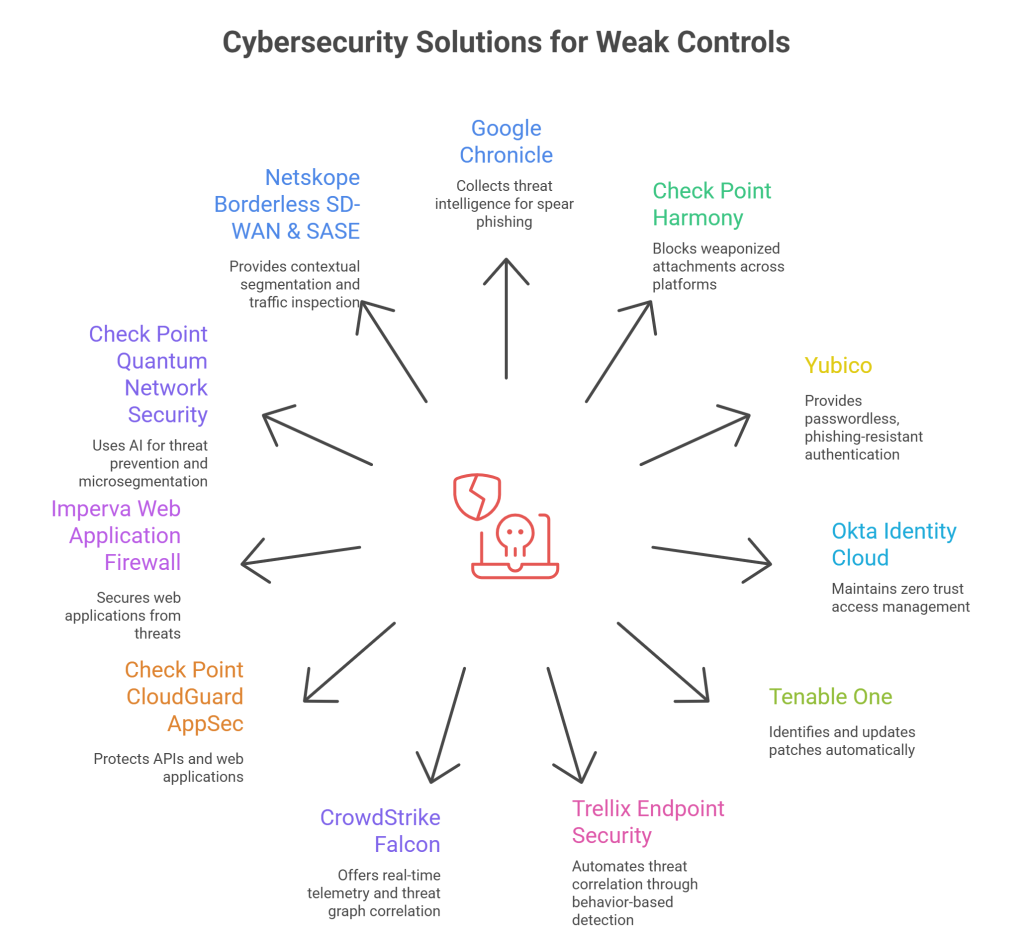
Lessons From APT36’s Tactics
By understanding their patterns and tactics, there are lots of lessons to be learned for Indian organizations when it comes to crafting their cybersecurity strategies:
Layer Your Defences: APT36 doesn’t just target one control at a time – their most devastating campaigns are multi-pronged in nature. Take an example with some of the aforementioned weak controls to see the cascading effect: they gain access through insufficient password policies & lack of MFA, then move laterally with ease across systems due to poor network segmentation, and wreak havoc while remaining undetected due to lack of effective monitoring. Their layered attacks need to be matched with layered defences of your own. That doesn’t mean getting as many security controls as possible – it’s about getting best-in-class solutions that tackle all the attack vectors your organization could face together.
Move From Reactive To Proactive: By the time groups like APT36 are inside your systems, it’s already too late. With that access, they could inflict damage upon your organization and the country as a whole. Therefore, reactive threat response should be made proactive through an effective threat hunting & threat intelligence strategy across all your controls, that monitor for anomalies and incidents. That way, you address potential attacks right at the outset before they cascade and get worse.
Get A Unified View: Ultimately, all these improved controls and threat intelligence platforms don’t amount to anything if they work in silos. You need a single platform that perpetually governs all these activities and gives you a unified view into threat insights as and when they are identified.
So, how does your organization go about making a portfolio of layered, proactive solutions with a unified view?
How do you go about crafting the solid cyber defence India needs in its critical infrastructure organizations during this time?
Build Control Maturity Within Your Organization
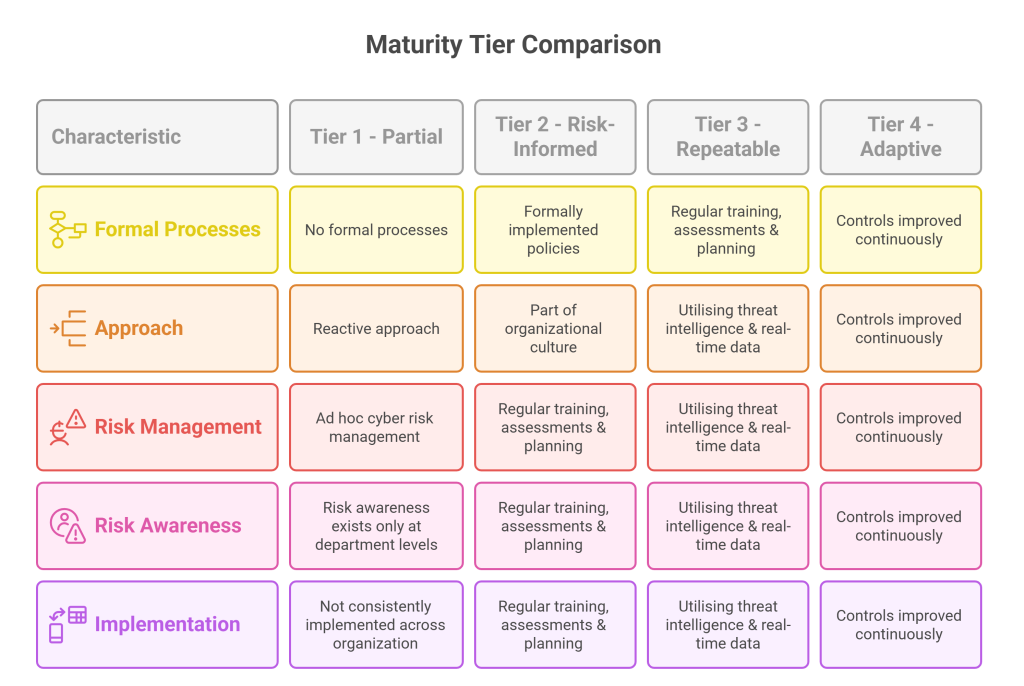
Control maturity measures the strength & reliability of your security controls over time, with processes to ensure linear growth for each control. There are many guidelines out there to measure it, but the prevailing one resides in the NIST Cybersecurity Framework. This divides each security control’s maturity into 4 tiers:
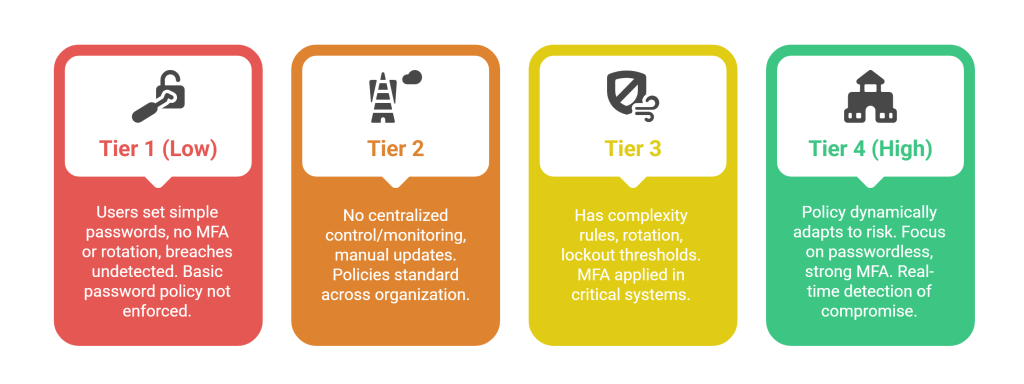
Let’s take the example of a specific control – your authentication policies – to show you how it evolves from low maturity to high maturity:
So, how do you go about building control maturity for all the security controls that groups like APT36 try to exploit?
Creating A Roadmap For High Control Maturity
Step 1: Identify your most vulnerable controls
Groups like APT36 have preferences in terms of controls they like to target. Many of them have been mentioned in the chart above, but each organization is different in terms of the kinds of specific vulnerabilities they have. The first thing to do would be conducting a general vulnerability assessment across your entire digital infrastructure – a tool like Tenable Nessus (which we at iValue provide in our control maturity suite) is the perfect starting point to identify your most vulnerable controls.
Step 2: Know which maturity tier you’re in for every control
Now that you’ve identified them, it’s time to check where each control is in the maturity tiers, from Tier 1 to Tier 4. Doing this exercise for all controls will help you further prioritize which controls need the most time devoted to making them mature.
Step 3: Create an implementation strategy to hit high maturity levels for each control
After conducting all these assessments, it’s finally time to start implementation. To achieve high maturity for all your controls, best-in-breed solutions must be used for each – something iValue specializes in. All these solutions are tailored to give your organization a proactive approach to identifying threats – the key is to feed all that threat intelligence into a 24×7 Security Operations Centre (SOC) that monitors & responds to any incidents as and when they arrive. This unified view is critical in improving the respective maturity levels of all your controls – a view we at iValue provide with our best-in-class managed SOC.
Step 4: Periodically audit to ensure continuous improvement
Set time periods when you re-evaluate these controls and ascertain where they currently are in the maturity level. It is important to know that the job isn’t done even when your controls reach Tier 4 maturity. Attack groups like APT36 use state-of-the-art tactics for their approaches, so to stay in Tier 4, you must continuously improve these controls to match current (& future) threat trends. We at iValue offer control maturity audits that go in-depth into what you should be doing to optimize these controls.
It’s a roadmap that will make you fully prepared to combat all kinds of cyber threats – click here to give your organization the best Control Maturity India has to offer with iValue’s suite.