The National Institute of Standards and Technology (NIST) has released version 2.0 of its influential Cybersecurity Framework (CSF).
First published in 2014, the NIST Cybersecurity Framework has become the most widely used cyber risk management framework globally. This new 2.0 version is the first revision in 10 years that includes updates that account for changes in cyber threats, technology, and cybersecurity practices over the past five years.
What is the NIST Framework?
The NIST Cybersecurity Framework is a voluntary risk management framework that provides a common language and set of guidelines for organizations to assess and improve their cybersecurity posture. It is designed to be flexible, scalable, and adaptable to organizations of all sizes and across various industries.
History of NIST Cybersecurity Framework
The journey of the CSF began with the Executive Order 13636 on February 12, 2013. It emphasized the importance of sharing cybersecurity threat information and creating a framework to reduce risks to critical infrastructure. Originally designed for critical infrastructure sectors, the CSF has been widely adopted by organizations across various industries.
NIST was tasked with developing the “Cybersecurity Framework”. The design criteria for the framework were:
- Identify Security Standards and Guidelines: The CSF aimed to identify applicable security standards across critical infrastructure sectors.
- Prioritized, Flexible, and Performance-Based Approach: It needed to provide a flexible, repeatable, and cost-effective method for managing cyber risk.
- Technology-Neutral Guidance: The CSF should be technology-neutral, allowing critical infrastructure sectors to benefit from a competitive market for products and services.
- Measuring Performance: It should guide organizations in measuring their implementation of the framework.
- Collaboration and Innovation: NIST, being an unbiased source of scientific data, collaborated with industry, academia, and other government agencies to ensure success.
Creating the Framework
NIST engaged stakeholders through a Request for Information (RFI) and Request for Comment (RFC). They identified existing cybersecurity standards, specified gaps, and collaboratively developed action plans. Over a year, NIST conducted workshops across the country to shape the CSF. The result was a framework that helps owners and operators of critical infrastructure assess and manage cyber risk effectively.
The framework is composed of 3 Main Components:
- Framework Core: A set of desired cybersecurity outcomes organized into Functions, Categories, and Subcategories. In 2014, NIST released the first version of the CSF, which focused on 5 functions under the framework core:
- Identify: Understand the cybersecurity risk to systems, assets, data, and capabilities.
- Protect: Develop and implement appropriate safeguards to ensure the delivery of critical infrastructure services.
- Detect: Implement activities to identify the occurrence of a cybersecurity event.
- Respond: Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
- Recover: Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
- Framework Implementation Tiers: A way to view and understand an organization’s cybersecurity risk management practices. The Framework Implementation Tiers describe the degree of rigor and sophistication of an organization’s cybersecurity risk management practices. The four Tiers are:
- Partial (Tier 1)
- Risk-Informed (Tier 2)
- Repeatable (Tier 3)
- Adaptive (Tier 4)
- Framework Profiles: A tool for aligning the Core’s outcomes with an organization’s specific business requirements, risk tolerance, and resources.
NIST CSF 2.0 – What’s New?
NIST Cybersecurity Framework 2.0 brings a deeper dive into governance, risk management, and security architecture, aiming to fortify cybersecurity postures and incident handling. Understanding these changes is crucial for implementing robust cybersecurity measures.
Some of the key changes in Cybersecurity Framework 2.0 include:
- New guidance on cybersecurity governance, aligned with ERM strategy setting
- Additional guidance on supply chain risk management
- Expanded identity management, authentication, and access control outcomes
- Updates to the Cybersecurity Framework Core categories and subcategories
- Greater focus on using Framework to communicate cyber risks enterprise-wide
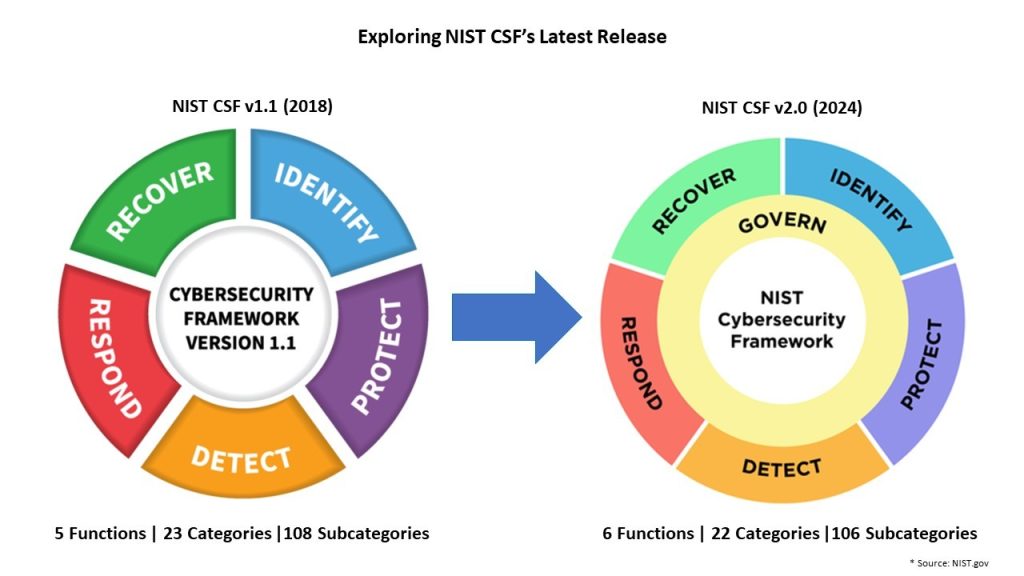
“Govern” function
One of the notable additions in NIST Cybersecurity Framework 2.0 is the introduction of the Govern function. This function plays a pivotal role in governance, providing a structured approach to managing cybersecurity risks effectively. Stakeholders need to pay attention to how this new function integrates with existing frameworks.
The governance function now encompasses six categories, incorporating elements from Asset Management, Business Environment, and more. Renaming categories like Business Environment to organizational context enhances clarity.
Increased Focus on Supply Chain Risk Management
The new “Cybersecurity Supply Chain Risk Management” Category within the Govern Function highlights the importance of managing risks associated with the global supply chain ecosystem.
Integration with Enterprise Risk Management (ERM)
CSF 2.0 provides guidance on integrating cybersecurity risk management with an organization’s overall ERM program.
Emphasis on Privacy Considerations
CSF 2.0 acknowledges the relationship between cybersecurity and privacy risks, encouraging organizations to consider both aspects in their risk management efforts.
Restructured Categories for Clarity
Version 2.0 showcases changes in categories and subcategories compared to the previous version. The framework has undergone realignments, removals, and renaming to refine its structure and focus. For instance, the incorporation of new categories like “Platform Security” emphasizes a holistic approach to protecting hardware, software, and services. Categories like Protective Technologies and Detection processes have been realigned for better organization. Governance aspects have been detailed with a focus on risk management, roles, policies, and oversight.
Key Updates in Identity
Certain categories have witnessed significant transformation in NIST Cybersecurity Framework 2.0. The consolidation of Improvement activities into one category under “Identify” signifies a broader scope in enhancing cybersecurity across functions. These changes emphasize the need for organizations to adapt and tailor their cybersecurity strategies accordingly.
Realignment and Streamlining
The framework has been streamlined in version 2.0 to improve clarity and practicality. Realignment of categories and subcategories ensures a more cohesive approach to cybersecurity management. For example, aligning previous concepts under the new “Incident Management” category prioritizes efficient handling of cybersecurity incidents.
Implications for Organizations
The changes in NIST Cybersecurity Framework 2.0 hold implications for organizations aiming to their cybersecurity posture. For businesses, the Cybersecurity Framework 2.0 provides an opportunity to evaluate how cyber risks are handled with other organizational risks like financial, reputational, privacy, etc. ERM calls for a holistic and coordinated view of all enterprise risks.
Adapting to the updated framework allows for greater alignment with current cybersecurity challenges and best practices. Organizations need to analyze these changes and implement them effectively to mitigate cybersecurity risks.
Here are some steps companies can take to leverage the new version:
- Review the Framework 2.0 and map cyber practices to it to identify any gaps
- Ensure cyber risk management strategy is aligned with organizational risk appetite
- Create system-level cyber risk registers that roll up into an enterprise-wide risk register
- Use core functions like Identity, Protect, and Detect to guide cyber risk activities
- Monitor cyber control effectiveness and give feedback to adjust Framework Profiles
- Use Framework to communicate cyber risks and requirements enterprise-wide
- Coordinate cyber risk management among leadership, managers, and practitioners
- Prioritize supply chain risk management and implement processes to assess and mitigate risks associated with their suppliers, partners, and third-party relationships.
- Revisit cybersecurity governance to align with the new Govern Function and its associated Categories and Subcategories.
The Cybersecurity Framework remains voluntary guidance and does not introduce new legal requirements. However, many businesses find value in adopting parts or all of the framework to strengthen their cyber defenses. CSF 2.0 gives organizations an updated blueprint to make risk-based decisions on cyber investments and resource allocation.
Adopting parts or all of Framework 2.0 can help strengthen cyber defenses while providing business leaders with better data to make risk-based decisions on cyber investments. The common language of the Framework supports communicating cyber risks effectively across the organization.
Expanded Online Resources: NIST has introduced new online resources, including Informative References, Implementation Examples, and Quick Start Guides, to assist organizations in adopting and implementing the CSF. You can read more in the NIST Cybersecurity Framework 2.0: Enterprise Risk Management Quick-Start Guide
